Your 2024 monthly money planner
Whether you’re coming across this page on New Year’s Day or during the holidays or anytime in between, you’ll find small steps to do each month — or any time — so you’ll know how to save money and reach your goals.

Whether you’re coming across this page on New Year’s Day or during the holidays or anytime in between, you’ll find small steps to do each month — or any time — so you’ll know how to save money and reach your goals.
Tax time is historically a prime opportunity for sneaky scammers. Jennifer Hessing, a fraud analytics director at Wells Fargo, shares these red flags to help you outsmart the latest tax fraud schemes.
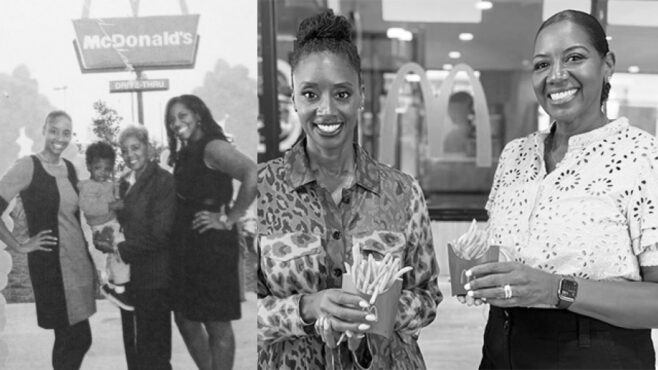
There were nearly 150,000 limited-service franchise establishments in the United States in 2017, and Wells Fargo has a dedicated team to help many of these future entrepreneurs start their business.

A single loan from Wells Fargo four decades ago helped a family build a thriving portfolio of 21 McDonald’s restaurants in South Los Angeles.

Although check crimes are on the rise, you have the power to avoid becoming a victim, starting with your pen. Joe Bernardo, Wells Fargo head of Fraud & Claims Operations, shares tips.

A new landscape for women-owned businesses has begun to appear over the past few years. They’re forming, increasing revenue, and employing more people faster than men-owned businesses, according to a Wells Fargo report. What’s changed?

If maintaining a carefully curated culture is a priority for your business when considering a succession plan, an ESOP may be a good option.

Have you considered starting your own business? Many dream of being their own boss, but the process can be daunting. Here is a breakdown of what you should do before you create a company.

Who will take on your business? It’s a question many experienced entrepreneurs must wrestle with to keep their business and family legacy alive. Here are a few ways to start.

The 2023 Jimmy & Rosalynn Carter Work Project was hosted by country music stars Garth Brooks and Trisha Yearwood.

For well over a century, Pioneer Linens — a longtime Wells Fargo customer — has evolved alongside its Palm Beach community. The secret to its success? A faithful family with a long legacy of caring about their customers.

Credits, deductions, and even saving and giving can help you reduce your taxable income before taxes are due and maximize your take-home pay.

From personal finance to networking to philanthropy, here are five tips to help you get ahead at work and in life.

More privacy. Optimized returns. More powerful technology. Quantum computers are on track to benefit Wells Fargo customers in the not-so-distant future.

Roughly one-third of Americans have become victims of cybercrime. Worried about your own risk of online financial fraud? Here are easy steps you can take to defend yourself.

After acquiring BrightStores in November 2022 with help from Wells Fargo’s technology banking team, OMG’s growth brings much-needed solutions to the branded merchandise space.

Warrior Rising, with funding from Wells Fargo, offers veterans mentoring, education, networking, and more as they pursue a path to business ownership.

New federal programs, paired with strategic budgeting, can give borrowers a fresh start at loan repayment.
 Medical transportation company reduces barriers to health care – one ride at a time
Medical transportation company reduces barriers to health care – one ride at a time Using blockchain to settle foreign exchange transactions
Using blockchain to settle foreign exchange transactions 5 big questions on quantum computing answered
5 big questions on quantum computing answered Artificial intelligence has the potential to reshape banking
Artificial intelligence has the potential to reshape banking Hacking for good: Meet the ethical hackers whose job it is to test Wells Fargo’s cybersecurity defenses
Hacking for good: Meet the ethical hackers whose job it is to test Wells Fargo’s cybersecurity defenses